How Can We Help?
Carbonetes Scan on Bitbucket Pipelines
Bitbucket Pipelines [1] is one of the tools used to build and test software automatically. It is easy to set up a CI/CD pipeline in Bitbucket with just a two steps configuration with built-in templates for several programming languages. It has also a feature called Bitbucket Pipes which are third-party tools that you can use for building your CI/CD pipelines more efficiently.
Bitbucket Pipes [2] can make a Bitbucket pipeline configuration clean and more efficient. Pipes are exclusively powerful when you want to deal with third-party tools. By just copying and pasting the pipe’s YAML syntax into your YAML file and providing the needed parameters for a specific pipe, the rest will be done by the Bitbucket Pipelines itself.
By using Carbonetes Scan [3] in Bitbucket Pipelines, it directly triggers a complete container analysis scan. The results of that analysis and the policy evaluation are placed right inside the Carbonetes Scan Pipe making it efficiently detect and resolve issues without ever leaving Bitbucket Pipelines, and you can also see all the results reflected simultaneously on Carbonetes dashboard [4].
The Most Comprehensive Security Analysis in the Market
Carbonetes Scan can provide all the results of analysis faster than our competition. It uses a larger number of pods [10] to analyze your images rather than using the old-fashioned constant way of scanning them. Other than providing results faster, Carbonetes Scan also provides best-in-class results of container security analysis. It also runs the analysis smoothly and continuously [11].
The Benefits of having Carbonetes Scan in your Bitbucket Pipelines
Carbonetes Scan is built into your Bitbucket Pipelines. You don’t have to waste time building your code through various security tools to check individual aspects of it. Carbonetes Scan can merge all container analysis into a single workflow that combines with your existing development workflow. Carbonetes Scan can trigger a complete container security analysis seamless and automatic. Upon building your images, it runs the analysis on your codes for security risks, checks the results against the policy, and builds or stops the build based on that policy evaluation [12].
Getting Started with Carbonetes Scan Pipe
Prerequisites
Using Carbonetes Scan requires valid Carbonetes credentials (email and password). You must also need to have an account on Bitbucket Pipelines and add the Carbonetes Scan right into your bitbucket-pipelines.yml file.
If you don’t have any credentials yet, you can register now.
How to use Carbonetes Scan on Bitbucket Pipelines
There are two ways to use Carbonetes Scan right into your Bitbucket Pipelines. One is pulling a Carbonetes Scan docker image from Dockerhub [6] and the other one is calling the pipe repo hosted on Bitbucket [7].
Example:
Pulling the Carbonetes Scan docker image from Dockerhub.
![]()
Calling the pipe repo hosted on Bitbucket.
![]()
Required Parameters and Values
To let Carbonetes Scan Pipe initiate a complete container analysis scan, it requires a few parameters. See the following required parameters and their values below.
- pipe: carbonetes/carbonetes-scan:1.0.1
variables:
CARBONETES_USERNAME: 'myusername@35.160.211.142'
CARBONETES_PASSWORD: ‘mypassword’
REGISTRY_URI: ‘12345678910.dkr.ecr.us-west-2.amazonaws.com'
REPO_IMAGE_TAG: ‘busybox:latest’
You can hide these values like `$CARBONETES_USERNAME` through the use of secured environment variables [8] inside your Bitbucket repository, to protect your credentials in Carbonetes.
See the table below for the description of each parameter.
| PARAMETERS | DESCRIPTION |
| CARBONETES_USERNAME * | The account username or email you use on Carbonetes. |
| CARBONETES_PASSWORD * | The account password on Carbonetes. |
| REGISTRY_URI * | Registry Uri (Added in Carbonetes web application) |
| REPO_IMAGE_TAG * | The image to be scan under your registry. |
* = required parameter
Writing Configuration for Bitbucket Pipelines
5.1 Modifying the bitbucket-pipelines.yml file
Bitbucket Pipelines has an online text editor and it has a specific tab for displaying the list of suggested pipes to be added right into your YAML file.
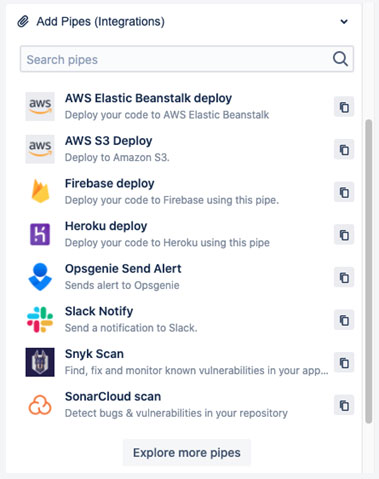
If you are new to Bitbucket Pipelines, please refer to the beginner guidelines [9].
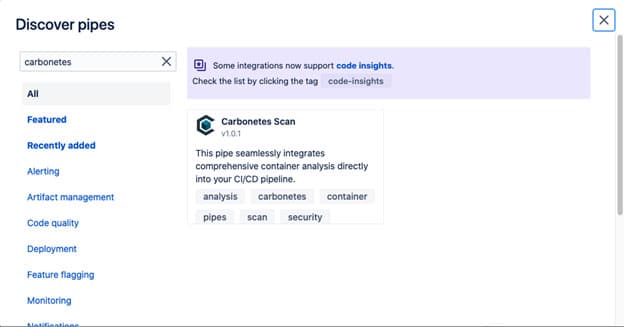
Next, just click the button “Explore more pipes” to see the list of all available pipes and search for Carbonetes.
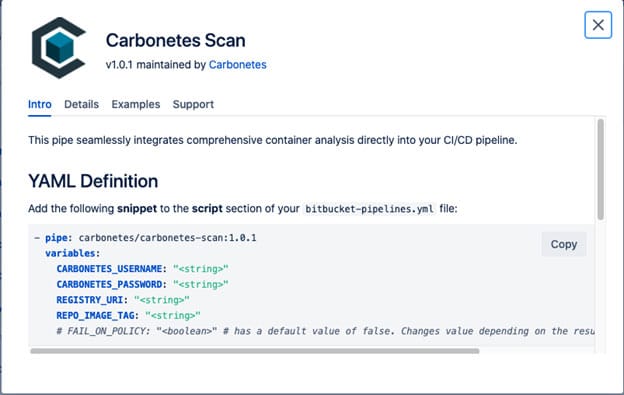
Click Carbonetes Scan to see the pipe’s details and explore it to understand how it works.
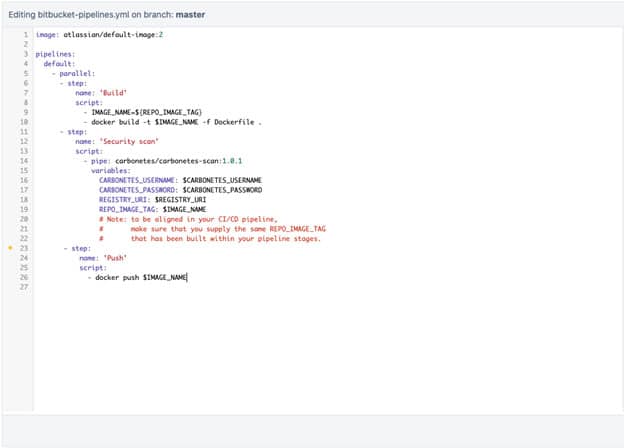
Copy and paste the given snippet to the script section of your bitbucket-pipelines.yml file. See the full example of YAML syntax below:
Note: to be aligned in your CI/CD pipeline, make sure that you supply the same REPO_IMAGE_TAG that has been built within your pipeline stages.
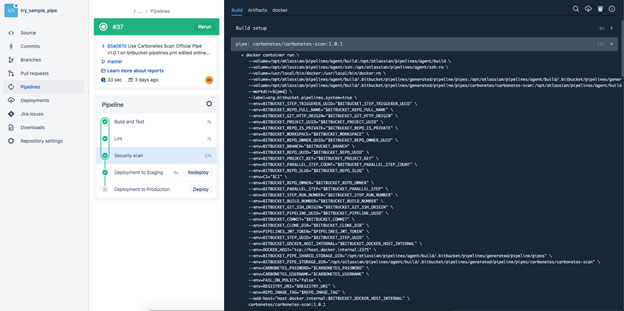
Lastly, save the changes to trigger the pipeline and head over to the Bitbucket Pipelines logs interface to see the results of the analysis.
Getting the Outcome
6.1 Results provided by Carbonetes Scan
The table below shows the different results after Carbonetes Scan finished checking all the known vulnerabilities of the scanned image.
| Result | Description |
| Vulnerabilities | A list of known security risks that can be exploited by a threat actor, listed with severities. |
| Software Compositions | Software that might cause a security risk listed with severities. |
| Software Dependencies | Pieces of software that rely on each other, listed with vulnerability counts. |
| Licenses | Legal compliances that are found on each software of the scanned image. |
| Malware | Virus threats that were found on the scanned image. |
| Secrets | Secret data found on each software of the scanned image. |
| Bill of Materials | A list of all the components that exist in software. |
| Policy Result | The result of the policy evaluation `PASSED` or `FAILED`. |
| Final Action | Decide if the build will `STOP` or `GO` based on the policy result. |
References:
[1] https://bitbucket.org/product/features/pipelines
[2] https://bitbucket.org/product/features/pipelines/integrations
[3] https://bitbucket.org/product/features/pipelines/integrations?p=carbonetes/carbonetes-scan
[4] https://console.carbonetes.com/dashboard
[5] https://app.carbonetes.com/register
[6] https://hub.docker.com/repository/docker/carbonetes/carbonetes-scan
[7] https://bitbucket.org/product/features/pipelines/integrations?p=carbonetes/carbonetes-scan
[9] https://support.atlassian.com/bitbucket-cloud/docs/get-started-with-bitbucket-pipelines/
