Blogs
Read our latest blog for insightful tips and knowledge!
Filter by
Infrastructure as Code (IaC)
What is Infrastructure as Code (IaC)? You can think of IaC as a universal configuration…
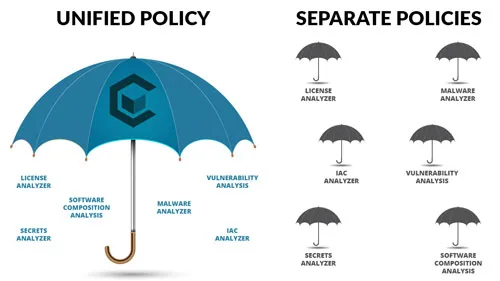
Choosing the Right Security Policy Solution
Security policies are a critical component of your security solution and selecting the right security…
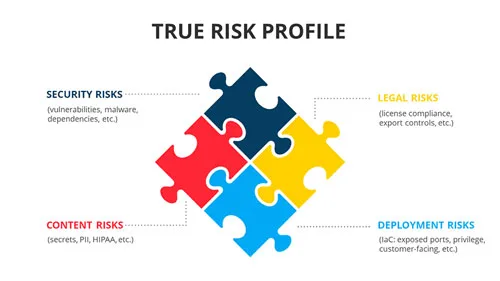
Container Security Asset Management
Container security is the practice of correlating all inherent security risks in conjunction with the…
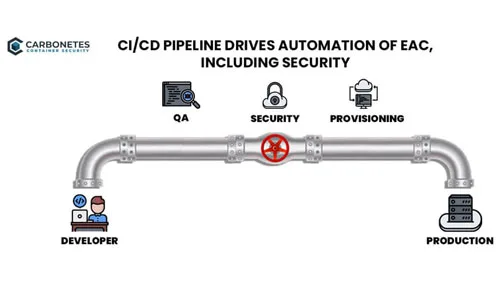
Security & CI/CD Toolchains
Modern security tools provide a variety of implementation options including full-function clients, APIs and CI/CD…

Container Security: Comprehensive Analysis vs. Specialty Analyzers
Securing a container involves analyzing for a variety of potential risks over a variety of…
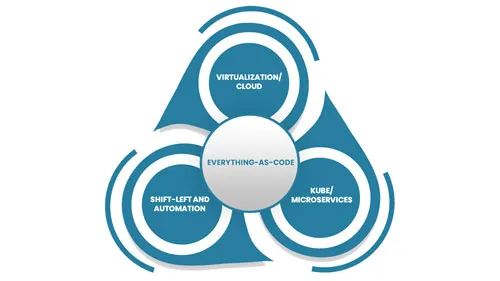
Everything-as-Code
Everything-as-Code (EaC) is the future of IT; the benefits are simply overwhelming. EaC is the…

The Parties Involved in Container Threat Model
Containerized applications are the cornerstone of modern software architectures. However, the complexity and dynamism of…

The Importance of Container Host in Maintaining Security in Containerized Processes
Container security is an essential aspect of maintaining an effective containerized process. A container host…
How Threats Can Easily Infiltrate Containerized Applications
Containerized applications are very vulnerable to threats even when they are not running. Here's how…

How Cloud Scanning Revolutionized Container Security
Cloud Scanning has become an essential component of any business' cybersecurity arsenal. Here's how it…
