Blogs
Read our latest blog for insightful tips and knowledge!
Filter by
No posts found.
5 Best Container Security Practices You Must Deploy
Containers have revolutionized the way applications are deployed and run. They offer many benefits over…

Infrastructure as Code (IaC) Auto-Remediation
Infrastructure as Code (IaC) is not as simple as some other security risks because IaC…
Infrastructure as Code (IaC)
What is Infrastructure as Code (IaC)? You can think of IaC as a universal configuration…
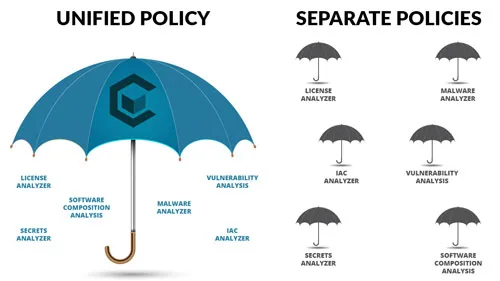
Choosing the Right Security Policy Solution
Security policies are a critical component of your security solution and selecting the right security…
