Blogs
Read our latest blog for insightful tips and knowledge!
Filter by
No posts found.
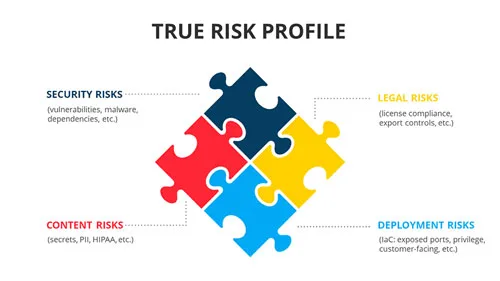
Container Security Asset Management
Container security is the practice of correlating all inherent security risks in conjunction with the…
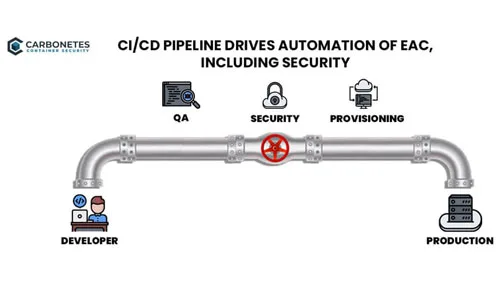
Security & CI/CD Toolchains
Modern security tools provide a variety of implementation options including full-function clients, APIs and CI/CD…

Container Security: Comprehensive Analysis vs. Specialty Analyzers
Securing a container involves analyzing for a variety of potential risks over a variety of…
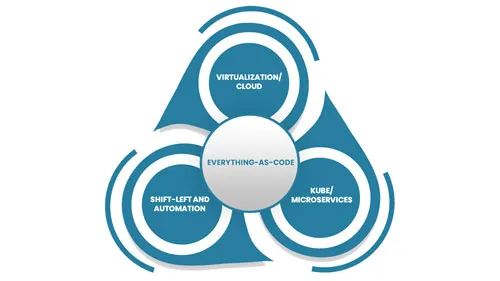
Everything-as-Code
Everything-as-Code (EaC) is the future of IT; the benefits are simply overwhelming. EaC is the…
