How Can We Help?
Carbonetes Comprehensive Analysis in Azure DevOps
Azure DevOps [1] was produced by Microsoft to allow software development companies to have DevOps capabilities upon creating software. It supplies version controlling, project management, and of course, a CI/CD pipeline they called Azure Pipelines.
Azure Pipelines [2] is designed to implement an automated building, testing, and deploying software and can support several programming languages as its base language. It also has a feature they call “Extensions”.
Extensions [3] are third-party tools or plugins that you can add right into your pipeline for some additional function. These extensions can easily communicate with Azure DevOps services by using Microsoft RESTful APIs [4].
Carbonetes is able to produce a fully managed security service as an extension [5] on Azure DevOps that triggers a comprehensive container analysis. It analyzes your container images for native code vulnerabilities, software composition analysis (SCA), license types, secrets, and bill of materials (BOMs).
The Most Comprehensive Security Analysis in the Market
Carbonetes Comprehensive Analysis can provide all the results of analysis faster than our competition. It uses a larger number of pods [8] to analyze your images -- rather than using the old-fashioned way of scanning them. Aside from providing results more expediently, Carbonetes Comprehensive Analysis also provides best-in-class results of container security analysis. Moreover, it runs the analysis smoothly and continuously.
The Benefits of having Carbonetes Comprehensive Analysis in your Azure Pipelines
Carbonetes Comprehensive Analysis is built into your Azure pipelines. You don’t need to waste a lot of time building your code using various security software to detect specific aspects of it. Carbonetes Comprehensive Analysis can put together all container analysis into a particular function that joins with your actual development function. Carbonetes Scan can prompt a comprehensive container security analysis seamless and automatic. Upon building your images, it runs the analysis on your codes for security risks, checks the results against the policy, and builds or stops the build based on that policy evaluation. For more information on our benefits, click here.
Getting Started
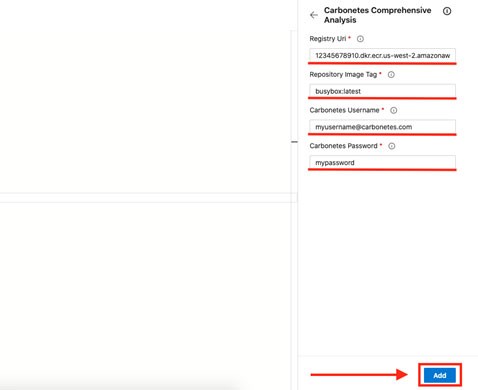
To enable Carbonetes Comprehensive Analysis right into your Azure Pipelines, you need to have an account on Azure DevOps [6]. In addition, valid credentials in Carbonetes are required.
If you haven't secured your credentials yet, you can register now.
See the table below for the required parameters.
| PARAMETERS | DESCRIPTION |
| username * | The account username or email you use on Carbonetes. |
| password * | The account password on Carbonetes. |
| registryUri * | The registry uri is managed in Carbonetes. |
| repoImageTag * | The image to be scanned under your registry. |
Writing Configuration for Azure Pipelines
Modifying the azure-pipelines.yml file
In order for Carbonetes to trigger the analysis, you must first install the Carbonetes Comprehensive Analysis Task Extension [5] within your Azure DevOps organization [7].
Proceed by following the steps to modify your azure-pipelines.yml file.
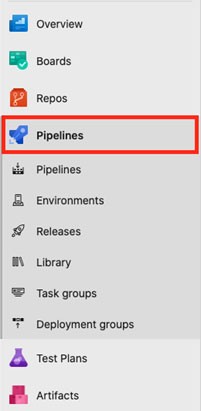
First, click the Pipelines section of the tab on the left side of the Azure DevOps interface.
Then, click the Carbonetes Task Extension and supply the needed information and click the “Add” button below.
Below is the automatically generated code after you supply the needed information and click the “Add” button.
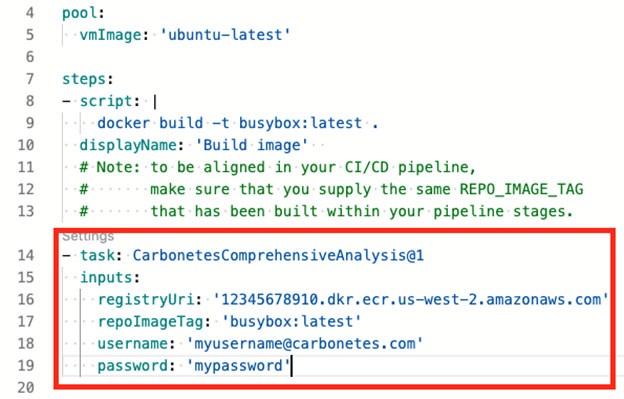
After modifying the azure-pipelines.yml file, save the changes to trigger the pipeline.
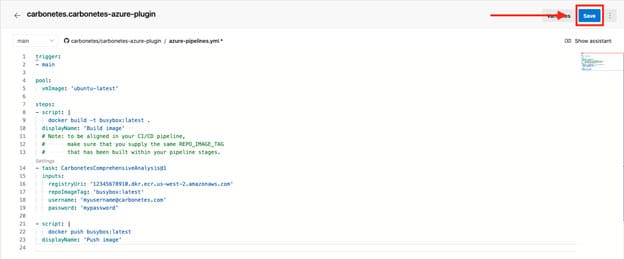
Lastly, you can navigate to the Azure DevOps logs interface to review the results of the analysis.
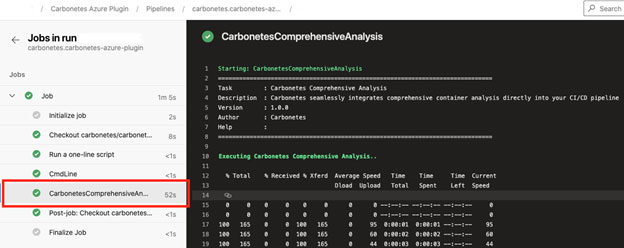
Getting the Outcome
Results provided by Carbonetes Comprehensive Analysis
The table below illustrates the various results upon Carbonetes checking all the known vulnerabilities of a scanned image:
| Result | Description |
| Vulnerabilities | A list of known security risks that can be exploited by a threat actor, listed with severities. |
| Software Compositions | Software that might cause a security risk listed with severities. |
| Software Dependencies | Pieces of software that rely on each other, listed with vulnerability counts. |
| Licenses | Legal compliances that are found on each software of the scanned image. |
| Malware | Virus threats that were found on the scanned image. |
| Secrets | Secret data found on each software of the scanned image. |
| Bill of Materials | A list of all the components that exist in software. |
| Policy Result | The result of the policy evaluation `PASSED` or `FAILED`. |
| Final Action | Decide if the build will `STOP` or `GO` based on the policy result. |
References
[1] https://azure.microsoft.com/en-us/services/devops/
[3] https://docs.microsoft.com/en-us/azure/devops/extend/overview?view=azure-devops
[4] https://docs.microsoft.com/en-us/rest/api/azure/devops/?view=azure-devops-rest-6.1
[5] https://marketplace.visualstudio.com/items?itemName=Carbonetes.carbonetes-comprehensive-analysis
