Blogs
Read our latest blog for insightful tips and knowledge!
Filter by

Continuous Monitoring in Container Security: Safeguarding Your Digital Ecosystem
Security is paramount in the containerized applications landscape, where agility meets complexity. Traditional security measures…
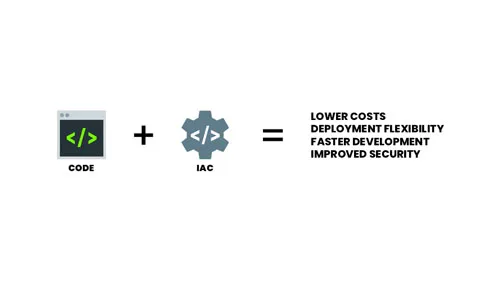
Infrastructure as Code (IaC)
What is Infrastructure as Code (IaC)? You can think of IaC as a universal configuration…

Infrastructure as Code (IaC) Auto-Remediation
Infrastructure as Code (IaC) is not as simple as some other security risks because IaC…

Embracing Zero Trust: A Paradigm Shift in Container Security for Web Applications
Security remains a paramount concern. Traditional security models are often insufficient to combat the sophisticated…
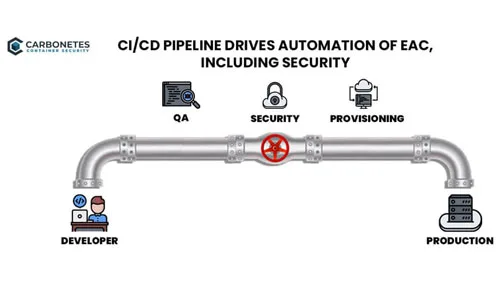
Security & CI/CD Toolchains
Modern security tools provide a variety of implementation options including full-function clients, APIs and CI/CD…
The Importance of Dependency Injection
Developers of the modern tech landscape are familiar with the concept of dependency injection and…

Continuous Monitoring in Container Security: Safeguarding Your Digital Ecosystem
Security is paramount in the containerized applications landscape, where agility meets complexity. Traditional security measures…

Embracing Zero Trust: A Paradigm Shift in Container Security for Web Applications
Security remains a paramount concern. Traditional security models are often insufficient to combat the sophisticated…

The Importance of SBOMs in Managing IoT Software Security
Building with open-source software is essential for many IoT developers. Open-source software provides a wealth…

Using IaC to Manage Edge Computing Infrastructure
Edge computing is the distribution of computing power and data storage closer to where data…
