Blogs
Read our latest blog for insightful tips and knowledge!
Filter by

8 Tips on Securing Your Codes and Its Dependencies Properly
Containerization has emerged as an effective way to secure your code and its dependencies. It’s…

Docker Registry: An Essential Tool for Container Image Management
Docker Registry is a critical component in the Docker ecosystem. It serves as a central…
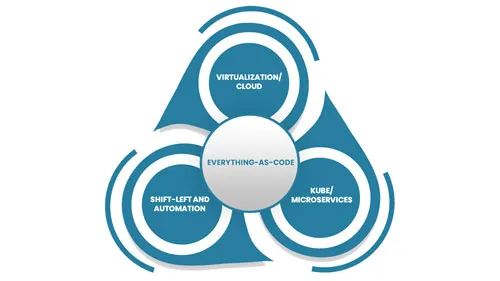
Everything-as-Code
Everything-as-Code (EaC) is the future of IT; the benefits are simply overwhelming. EaC is the…

6 Advantages of Open-Source Container Security
Open-source container security has many advantages over traditional security models. Let's look at some of…

How Cloud Scanning Revolutionized Container Security
Cloud Scanning has become an essential component of any business' cybersecurity arsenal. Here's how it…

How Container Security Platforms Help in the Aftermath of a Security Threat
In today's interconnected digital landscape, where security threats loom large, organizations continually seek robust solutions…

Keeping Your Docker Secrets a Well-Kept Secret
Docker Secrets are config files that contain sensitive information, like passwords, tokens, and keys. Unlike…

The Importance of Container Runtime
When you talk about container security, a critical component inevitably comes up: container runtime. But…

The Importance of Constant Container Security Scanning
The age of containerization has ushered in a new era of container security: one where…

Why AWS Misconfiguration Should Be Avoided at All Cost
When securing your business online, no one does it like AWS (Amazon Web Services). With…
